FAQ
What kind of secret type patterns does the app detect?
A list of secret type patterns that No More Secrets uses to detect secrets:
Category | Name | Description |
|---|---|---|
Personal Identifiable Information | Social Security Number | Personal identification number used in the United States |
IBAN | International bank account number. IBAN numbers are made of up to 34 alphanumeric characters, consisting of a two digit country code, two check numbers, up to six digits for the bank code, up to six digits for the bank branch code and up to eleven characters for the bank account number | |
Credit Card Patterns | American Express Card | American Express card numbers start with 34 or 37 and have 15 digits |
Discover Card | Discover credit card numbers begin with 6011 or 65 and have 16 digits | |
Maestro credit card | Maestro credit card number | |
Mastercard | MasterCard numbers either start with the numbers 51 through 55 or with the numbers 2221 through 2720. All have 16 digits | |
Visa Credit Card | Visa credit card numbers start with a 4. New cards have 16 digits. | |
Technology credentials and secrets | PKCS8 Private Key | PKCS8 Private Key |
RSA Private Key | RSA Private Key | |
OPENSSH Private Key | OPENSSH Private Key | |
PGP Private Key | PGP Private Key | |
SSH-DSA Private Key | SSH (DSA) Private Key | |
SSH-EC Private Key | SSH (EC) Private Key | |
GitHub Personal Access Token | GitHub Personal Access Token | |
GitHub OAuth Token | GitHub OAuth Access Token | |
GitHub App Token | GitHub App Token | |
GitHub Refresh Token | GitHub Refresh Token | |
Slack Access Token | Slack Access Token | |
New Relic User API Key | New Relic User API Key | |
New Relic Browser API Token | New Relic ingest browser API token | |
Postman API token | Postman API token | |
Rubygem API token | Rubygem API token | |
Cryptographic private key | The ".pem" file extension is used for storing certificates and private keys | |
Cryptographic key bundle | These file extensions are potential cryptographic key bundles | |
OpenVPN client configuration file | The ".ovpn" file extension is used for OpenVPN client configuration | |
Microsoft BitLocker key | Microsoft BitLocker recovery key file | |
Password Safe database file | Password Safe database file | |
Java keystore file | Java keystore file | |
Apple Keychain database file | The ".keychain" extension is an Apple Keychain database file, used for storing passwords | |
KDE Wallet Manager | KDE Wallet Manager database file | |
Shell configuration file | Shell configuration files can contain passwords, API keys, hostnames and other secrets | |
Environment configuration file | The ".env" file extension is used for storing configuration data, which often includes secrets | |
Potential Linux passwd file | "passwd" files contain system user information | |
Amazon MWS auth token | Amazon Marketplace Web Service auth token | |
AWS API key | Amazon Web Services API key | |
Facebook access token | Facebook access token | |
Google API key | Google Drive, Gmail, YouTube, or Google Cloud Platform API key | |
Google OAuth | Google Drive, Gmail, YouTube, or Google Cloud Platform OAuth credentials | |
Square access token | Square payment platform access token | |
Square OAuth secret | Square payment platform OAuth secret | |
Twitter access token | Twitter access token | |
Azure storage key | Azure Storage Account access key | |
General Patterns | ||
Filename contains word: credential | The attachment filename contains the word: "credential", which is associated with login secrets | |
Filename contains word: password | The attachment filename contains the word: "password" |
During the “allow access” process, there is a list of permission scopes that I need to allow access for. Are all of these necessary?
Atlassian has recently changed how app permissions work, requiring apps to request more detailed permission scopes for the data they have access to.

Why is each of these permission scopes required?
In Jira
Delete
Delete issue properties. No More Secrets uses issue properties for storing attachment scan results – these scan results are deleted when an attachment is removed from the issue.
View
View various fields and data related to Jira issues. No More Secrets scans text-based field values and comments in Jira issues. To do this, the app requests issue data. Not all of the data are used by No More Secrets, but Jira requires all of these granular scopes enabled to be able to fetch any issue data.
View issue properties. These permissions are required for the storage and retrieval of attachment scan results.
View attachment permission is required for the upcoming attachment content scanning feature.
View all projects with issue search for the project scanner
Update
Create and update issue properties. No More Secrets uses issue properties for storing attachment scan results. The app updates these scan results if the patterns used for secret detection change.
Send
Send email notifications when a new issue or new comment is created that includes potential secrets.
In User
View the currently logged in user. This is a general permission required for user-facing apps, and is necessary for the app’s “custom field” component.
Who gets email notifications about detected secrets?
When a new issue is created that includes secrets, the reporter of the issue will receive an email notification.
Also, when a new comment that includes a secrets is added to an issue, the author of the comment will receive an email notification.
Finally, when an attachment that includes secrets is added to an issue, the author of that addition will receive an email notification.
Why am I not receiving email notifications about detected secrets?
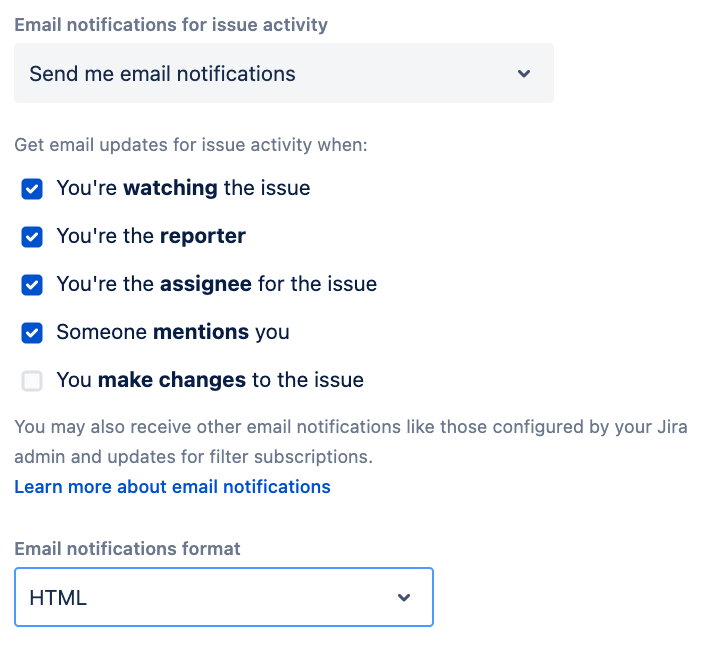
Check personal settings (Click on Avatar > Jira Personal Settings) to ensure “Send me email notifications” is enabled and choose the email notification notifications format of preference.
Also, check that the project itself has the project role atlassian-addons-project-access included in each of the project permissions
What is the max attachment file size that the app can scan for secrets?
The app can scan attachments up to and including file sizes of 25 MB
Which attachment file types are scanned for secrets within their content?
The app can scan the contents of text type file attachments. All other file types will be excluded from attachment content secret scanning.
Why is the custom field not visible for my team-managed project?
Atlassian currently only supports the custom fields to be available for company-managed & service management projects. However, if secrets are added to team-managed project issues, the reporter of the issue will be notified that secrets have been detected in the issue. The same applies if new comments or attachments with secrets are added to existing issues, the author of those additions will be notified with an email.
Does No More Secrets for Jira need special project permissions?
The app requires the atlassian-addons-project-access project role to have permission to all projects that need to be scanned for secrets. To check if this project role is included, go to Project Settings > Permissions.
Note: For the automated scanning of new attachments (and sending email notifications), this permission is used by the app. For the No More Secrets Project Scanner, the logged-in user conducting the scan must have access to the project(s). Only projects the user has permission to access will return issue scan results.
